Cyber Insurance: Empowering Risk Management in the Digital Age - Webinar Recap
The digital landscape brings immense opportunities for businesses but also exposes them to increasing cyber threats. As cyberattacks grow in sophistication, organizations must adopt proactive measures to safeguard their assets and data. Cyber insurance has emerged as a crucial component of risk management, offering financial protection and support in the face of cyber incidents. In this comprehensive recap of a webinar featuring experts Lewis Evans and David Kruse, we explore the world of cyber insurance, its significance, key considerations, and how organizations can secure optimal coverage.
Understanding Cyber Insurance
Cyber insurance, also known as cybersecurity insurance or cyber liability insurance, provides specialized coverage against financial losses arising from cyber-related incidents. These incidents include data breaches, ransomware attacks, business interruption due to cyber incidents, network outages, and other cyber losses.

The Importance of Cyber Insurance:
Cyber insurance plays a vital role in risk management due to several factors:
· Financial Protection: Cyberattacks can result in significant financial losses, encompassing legal fees, recovery costs, ransom payments, and potential lawsuits. Cyber insurance offers financial support to mitigate these expenses.
· Business Continuity: Major cyber incidents can disrupt business operations, leading to downtime and lost revenue. Cyber insurance can provide compensation for income losses during such periods.
· Risk Transfer: Cyber insurance shifts some of the risk associated with cyber incidents from the business to the insurer, providing peace of mind to business owners and stakeholders.
· Compliance Requirements: In certain industries, cyber insurance may be mandatory for regulatory compliance, demonstrating an organization’s commitment to cybersecurity.
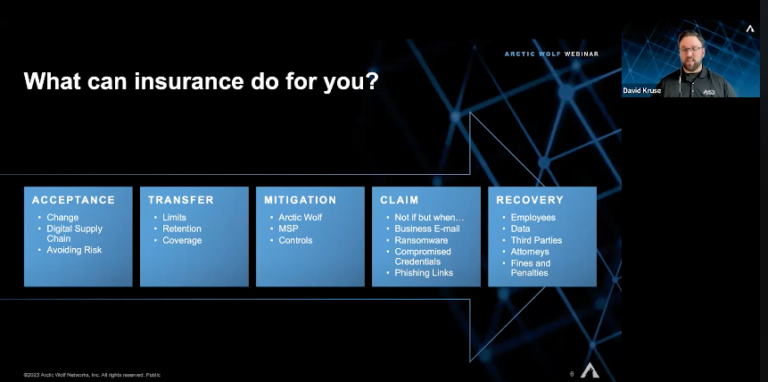
Choosing the Right Cyber Insurance Policy
Selecting the appropriate cyber insurance policy requires careful consideration of specific organizational needs. Key factors to assess include:
· Coverage Limits: Evaluating coverage limits to align with potential cyber risk exposure.
· Incident Response Coverage: Checking if the policy includes incident response services, such as forensic investigations, legal counsel, and public relations support.
· Business Interruption Coverage: Ensuring the policy covers business interruption losses resulting from cyber incidents.
· Ransomware Coverage: Verifying if the policy includes ransom payments and extortion expenses.
· Third-Party Liability: Considering the extent of third-party liability coverage, encompassing costs related to legal claims and regulatory fines.
· Compliance Requirements: Ensuring the policy meets relevant cybersecurity regulations and compliance obligations for the industry.
The Cyber Insurance Market
The cyber insurance market has expanded rapidly in response to the escalating cyber threat landscape. As a result, insurers offer various coverage options and tailored policies to meet diverse business needs. Staying informed about market trends is essential, as they can impact policy availability and premiums.
Enhancing Insurability: The Role of Security Capabilities
Robust security capabilities are critical in demonstrating insurability and obtaining favorable insurance terms. Insurers evaluate security controls and risk mitigation measures during the underwriting process. Implementing comprehensive security measures can significantly reduce the frequency and severity of cyber incidents, making organizations more attractive candidates for cyber insurance.
Crafting a Compelling Risk Story
The art of risk storytelling is essential in securing favorable insurance terms. A well-crafted risk story outlines an organization’s proactive security measures, ongoing cybersecurity improvements, and lessons learned from past incidents. Demonstrating a clear commitment to risk reduction can significantly influence insurance underwriters’ decisions.
Navigating the Underwriting Process
The underwriting process plays a pivotal role in determining insurance coverage and premiums. It involves assessing an organization’s risk profile, security posture, and overall insurability. A robust risk story, combined with evidence of effective security controls, improves the chances of securing favorable coverage and premiums.
The Role of Security Operations
Investing in security operations is crucial in reducing the frequency and severity of cyber incidents. A comprehensive security operations platform offering continuous monitoring, threat detection, and incident response capabilities can enhance insurability. Integration with existing security tools ensures comprehensive coverage and real-time insights.
In conclusion, by investing in robust security capabilities, crafting compelling risk stories, and partnering with reputable security operations providers, organizations can navigate the cyber insurance landscape confidently. Cyber insurance, combined with effective risk management, is the key to protecting digital assets and maintaining a resilient and secure business in the dynamic digital age.




